Vulnerability Assessment and Compliance Verification
by Andrew Kroh
OpenSCAP is an open source tool for performing automated vulnerability assessment and policy compliance verification on linux. SCAP, pronounced “ess-cap”, is the Security Content Automation Protocol which pulls together open standards for describing vulnerabilities like CVE, CVSS, OVAL, and XCCDF. The OpenSCAP tool, which is NIST certified, ingests the SCAP content and outputs a report of which checks passed and failed.
Let's walkthrough an example of how to audit a RedHat 6 machine against SCAP content provided by DISA known as the Redhat 6 STIG Benchmark.
First, you need to install OpenSCAP and its dependencies (and I'm installing wget and unzip so that I can download the STIG and unzip it).
$ yum install openscap-utils wget unzip
================================================================================
Package Arch Version Repository Size
================================================================================
Installing:
openscap-utils x86_64 1.0.8-1.el6_5.1 rhel-x86_64-server-6 52 k
unzip x86_64 6.0-1.el6 rhel-x86_64-server-6 149 k
wget x86_64 1.12-5.el6_6.1 rhel-x86_64-server-6 483 k
Installing for dependencies:
bzip2 x86_64 1.0.5-7.el6_0 rhel-x86_64-server-6 49 k
elfutils x86_64 0.158-3.2.el6 rhel-x86_64-server-6 233 k
elfutils-libs x86_64 0.158-3.2.el6 rhel-x86_64-server-6 211 k
fakeroot x86_64 1.12.2-22.2.el6 rhel-x86_64-server-6 73 k
fakeroot-libs x86_64 1.12.2-22.2.el6 rhel-x86_64-server-6 23 k
file x86_64 5.04-21.el6 rhel-x86_64-server-6 47 k
gdb x86_64 7.2-75.el6 rhel-x86_64-server-6 2.3 M
libxslt x86_64 1.1.26-2.el6_3.1 rhel-x86_64-server-6 452 k
man x86_64 1.6f-32.el6 rhel-x86_64-server-6 263 k
openscap x86_64 1.0.8-1.el6_5.1 rhel-x86_64-server-6 2.9 M
patch x86_64 2.6-6.el6 rhel-x86_64-server-6 91 k
perl x86_64 4:5.10.1-136.el6_6.1 rhel-x86_64-server-6 10 M
perl-Module-Pluggable x86_64 1:3.90-136.el6_6.1 rhel-x86_64-server-6 40 k
perl-Pod-Escapes x86_64 1:1.04-136.el6_6.1 rhel-x86_64-server-6 32 k
perl-Pod-Simple x86_64 1:3.13-136.el6_6.1 rhel-x86_64-server-6 212 k
perl-libs x86_64 4:5.10.1-136.el6_6.1 rhel-x86_64-server-6 578 k
perl-version x86_64 3:0.77-136.el6_6.1 rhel-x86_64-server-6 51 k
rpm-build x86_64 4.8.0-38.el6_6 rhel-x86_64-server-6 127 k
rpmdevtools noarch 7.5-2.el6 rhel-x86_64-server-6 109 k
xz x86_64 4.999.9-0.5.beta.20091007git.el6
rhel-x86_64-server-6 137 k
xz-lzma-compat x86_64 4.999.9-0.5.beta.20091007git.el6
rhel-x86_64-server-6 16 k
Updating for dependencies:
elfutils-libelf x86_64 0.158-3.2.el6 rhel-x86_64-server-6 182 k
file-libs x86_64 5.04-21.el6 rhel-x86_64-server-6 313 k
rpm x86_64 4.8.0-38.el6_6 rhel-x86_64-server-6 902 k
rpm-libs x86_64 4.8.0-38.el6_6 rhel-x86_64-server-6 313 k
rpm-python x86_64 4.8.0-38.el6_6 rhel-x86_64-server-6 57 k
xz-libs x86_64 4.999.9-0.5.beta.20091007git.el6
rhel-x86_64-server-6 89 k
Transaction Summary
================================================================================
Install 24 Package(s)
Upgrade 6 Package(s)
Total download size: 21 MNow with the tool installed we can audit our server against the DISA STIG. The DISA STIG can be downloaded from DISA’s web site.
$ wget http://iase.disa.mil/stigs/Documents/U_RedHat_6_V1R6_STIG_SCAP_1-1_Benchmark.zip
$ unzip U_RedHat_6_V1R6_STIG_SCAP_1-1_Benchmark.zip
$ oscap info U_RedHat_6_V1R6_STIG_SCAP_1-1_Benchmark-xccdf.xml
$ oscap xccdf eval \
--report `hostname`-redhat_6_v1r6_stig.html \
--cpe U_RedHat_6_V1R6_STIG_SCAP_1-1_Benchmark-cpe-dictionary.xml \
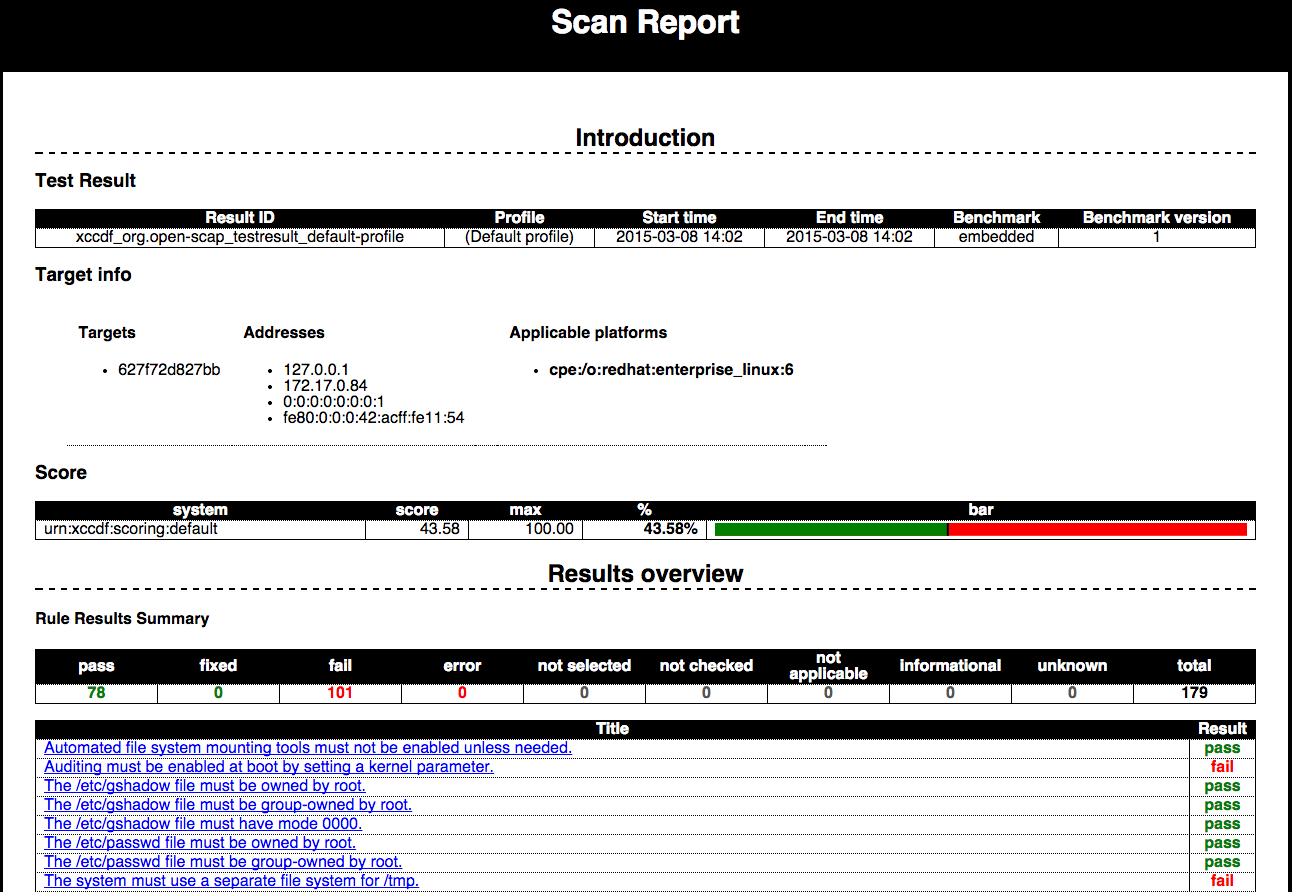
U_RedHat_6_V1R6_STIG_SCAP_1-1_Benchmark-xccdf.xmlThe HTML report that is generated can be viewed in the browser. It summarizes each rule with a simple pass/fail result. There are details for each rule and remediation instructions.
Another useful test for RedHat systems is to verify that all of the required patches have been installed to address the RedHat security advisories, RHSA (you can subscribe for announcements here.
$ wget http://www.redhat.com/security/data/oval/com.redhat.rhsa-all.xml
$ oscap oval eval \
--results rhsa-results-oval.xml \
--report `hostname`-rhsa-report.html \
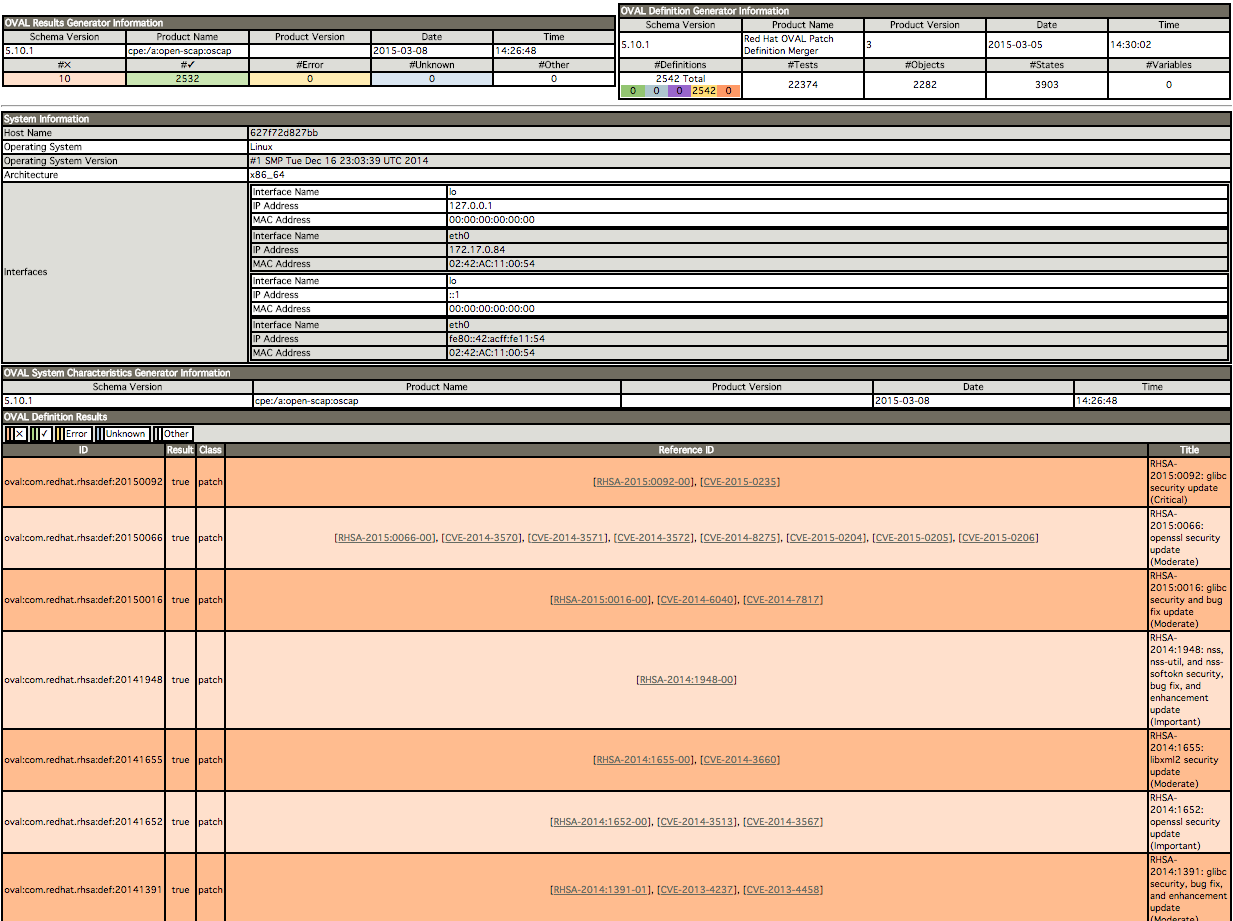
com.redhat.rhsa-all.xml Again, you can view the report in the browser to see what patches have been applied and what patches need to be applied.
Subscribe via RSS